Tutorial
Creating security groups
Instances in heiCLOUD are located behind a firewall. This firewall receives its rules from a security group. Depending on how you want to access an instance, you need to create security groups with the rules you require. By default only the security group named "default" exists
In order to access an instance from the outside an appropriate security group is required in addition to an assigned Floating-IP ("Launching Instances" Point 11). By default instances are only allowed to establish outgoing connections (e.g. for updates). All Incoming connections are blocked. To allow these e.g. for SSH, RDP or HTTP(s) connections proceed as follows:
- Log in to heiCLOUD.
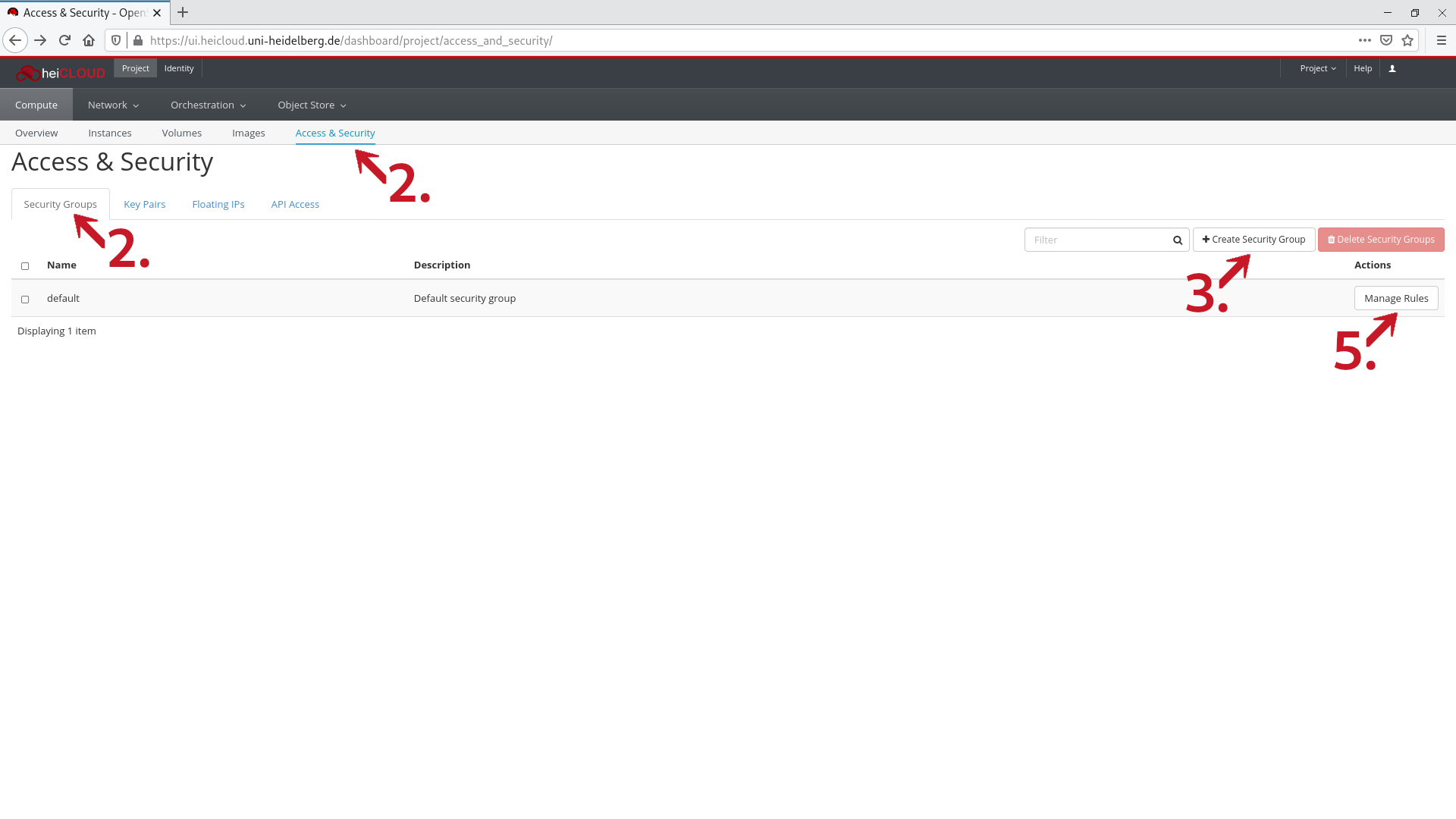
- Under Project → Compute, click on Access & Security. Click on the Security Groups tab. You will see an overview of your (existing) security groups.
- (Optional) In the top right, click on the Create Security Group button. A new window will open.
- (Optional) Enter a name for the security group (e.g. SSH-Access).
- To manage a security group, click on the Manage Rules button to the right in the row of the relevant security group. A new window will open.
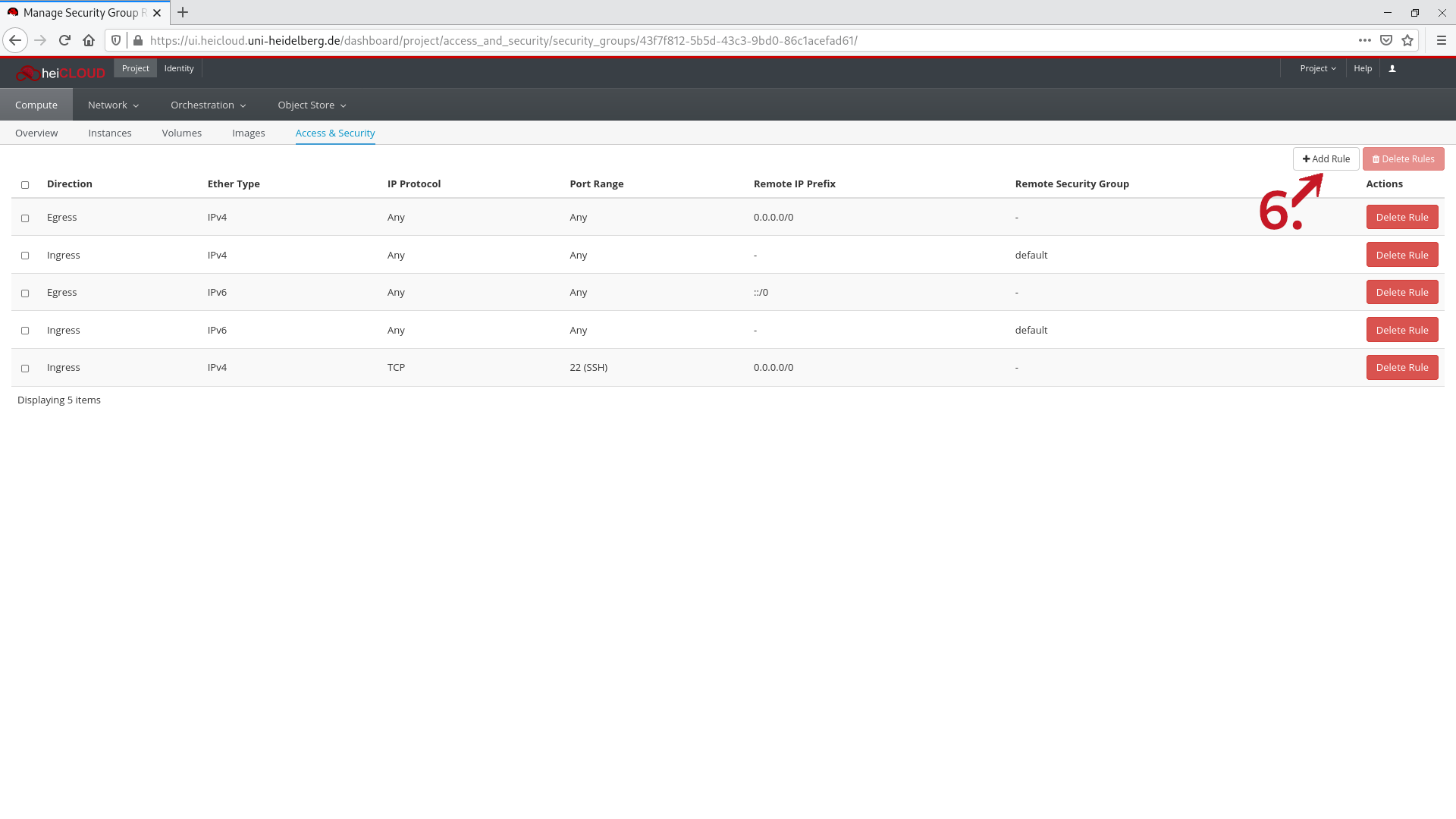
- To add a new rule click the Add Rule button in the top right. A new window will open.
- In the Rule drop-down menu, select the protocol for which you want to open a port. To allow remote access to your instance the following rules are required:
- (Linux) To enable SSH access select SSH.
- (Windows) To enable RDP access select RDP.
- (optional) In the CIDR box, you can choose an address range from which access is possible. By default, worldwide access is possible ("any", 0.0.0.0/0). To limit access to the university network, create two identical rules, specifying an address range of 129.206.0.0/16 for the first and 147.142.0.0/16 for the second.
For Windows (RDP access) it is strongly recomended to use this option to limit access to the university network or ideally the IP of your workstation!
- Click on Add to complete the process.
If you need more forwardings e.g. for HTTP or HTTPS you can repeat the steps above selecting the appropriate rule (point 7).
For security reasons please keep the number of forwardings as well as the permitted IP ranges as small as possible!
Databases like MySQL, MongoDB or Elasticsearch or cache software like Varnish or Memcached should never be accessible directly from the outside.